Testing and Fixing Security vulnerabilities for Web Applications
A Case Study Using OWASP ZAP
Web Application's consumers and businesses are nervous about the security risks of the internet. These security risks can damage user's social Image & brand value of business. Cyber criminals have evolved several techniques to threaten privacy and integrity of bank accounts, businesses, and organizations.
Now User's data and Information's security has become prime concern for businesses and communities to have satisfied customers.
Technology angle : HTTP protocol being stateless, becomes easy target for attackers to try some malicious activities to damage Data available over Web.
Some major threats are:
1- Cross Site Scripting (XSS- attacks):-XSS is considered to be most common threat where attacks are injected in form of scripts through User Forms or any other interface which takes user's input. These malicious scripts are then executed on target machine and can cause damage to infrastructure, and data.
2- SQL injection:- SQLi is also common way to attack data available on public domain by executing exposed SQL commands on target System to expose or damage data.
3- Remote OS Command Injection :-ROCi attack is possible when an application accepts untrusted input to build operating system commands in an insecure manner.
4- Cookie Injection / Session Hijacking
5- Denial Of Service attack... read more about threats here
Step 1- Figuring out what vulnerabilities exist in your current system
There are many opensource tools available to detect security vulnerabilities. OWASP is one of very popular opensource tool to detect any open end points exposed to security threats.
This tool generates report with all vulnerabilities in the form of Alerts, which current system might be exposed to.
Step 2- Fixing the issues in existing system running in Production
Its always easier to design the threat Proof system from scratch by keeping few simple rules in mind while designing new system. Like
1- Strict Type Checking at front end and Back End : All data validation scheme should be implemented at both level, front as well as back End. There is a need of close collaboration between front End and Back End Teams. DB schema designers must keep all Front End team's in loop about all exposed keys, their relationship and validations. Back End Services must be designed with strong type check in such a way that they are not vulnerable to any security threat even when exposed to any interface other than your own Front End interface.
2- Redirect URLs White List : Cross Domain URL redirects should be handled with extra care. Cross Domain Redirect including Emails must allow the URLs from a predefined white list of domains.
3- Hiding Applications Errors from Users: Exceptions details should never be exposed to End User. There should be proper mapping of Exception messages/ Exception Codes with User Understandable Plain Message, which are wrapped with responses.
a-) Embedding Exceptions StackTrace with Response is a Strint NO. Exceptions Stack Traces can be added to logger, along with other parameters causing Exception.
b-) Parameter Validation Messages should never reveal all correction methodology or internal variable names.
Now think of situation where, system is already running in production, and you have tried all validations at client side with out touching the logic at back-end worrying that it might break core business logic and still not able to protect system completely from the threats.
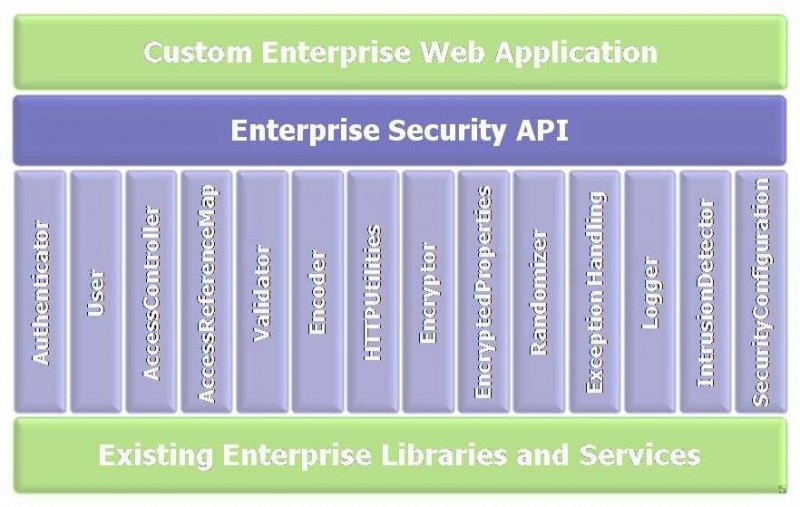
In such situations, it becomes important to fix the back end using the Abstracted Validation Layer above the Application's Core business Logic. We are taking here ESAPI for example which acts as gateway to provide security services to protect your application from external threats.
Following services can be used to protect system from vulnerabilities
Shown here is the ESAPI Validator, Encoder service to protect the application from XSS security threats.
1- Invalidating the unintended request: Using ESAPI we can define custom validator API for Java or Python based applications. These API's can easily validate a type of input parameters matching against a regular expression of filter criteria.
Sample code:
ESAPIValidatorUtil.validateSafeText_ESAPI(Request Parameter to be validated comma seperated );
Here validateSafeText_ESAPI() is a custom API written to validate all text based HTTP request, against a valid regular expression defined in ESAPI.properties file.
2- Handling Threats instances: While detecting any security vulnerability, our application should be prepared to handle any such instance. OWASP's App Senser Utility can detect any such instance of malicious activity
Sample code
if (ESAPIValidatorUtil.detect(password, message)) {
new AppSensorException("CLassName", "An error has occurred.", "Possible intrusion attempt detected.");
}
Similarly any of services could be utilized to protect the system, as an added layer of security above Application's Business Layer.